February 2023 | 777 words | 2-minute read
In today’s digital-driven lifestyle, we frequently use browsers on our devices to transact – to buy goods and services or transfer funds. Even as you transact, a series of activities take place behind the scenes: transaction requests are sent to servers; various validation criteria are applied and if found valid, these are executed; storing the result on the server. A response is sent to you on the browser and you know that your transaction has been successful. As you know, all this happens within a matter of seconds.
Before the emergence of Distributed Ledger or DLT and Blockchain technologies, automating processes across business enterprises was difficult, unless a trusted third-party was involved – for example an intermediary payment gateway. Even when there was a trusted third-party partner such processes were frequently slow and error-prone and hence expensive. The primary business case, then, for DLT or Blockchains technology derives from its ability to automate processes that work across businesses by eliminating the need for third parties or making them more efficient. Fundamentally DLT/Blockchains ensure ‘What You See Is What I See’ (WYSIWIS) and ‘What I See Is What You See’ (WISIWYS) at each step of such processes, making them much more efficient and effective.
Types of DLTs and Blockchains
There are multiple DLT/Blockchain technologies. In DLT applications a transaction request can be submitted to multiple servers or counterparties. If these requests are valid and if there is consensus of the majority among the servers regarding this validity, the requests are executed; and the result is stored on the server. A success response is returned to the user.
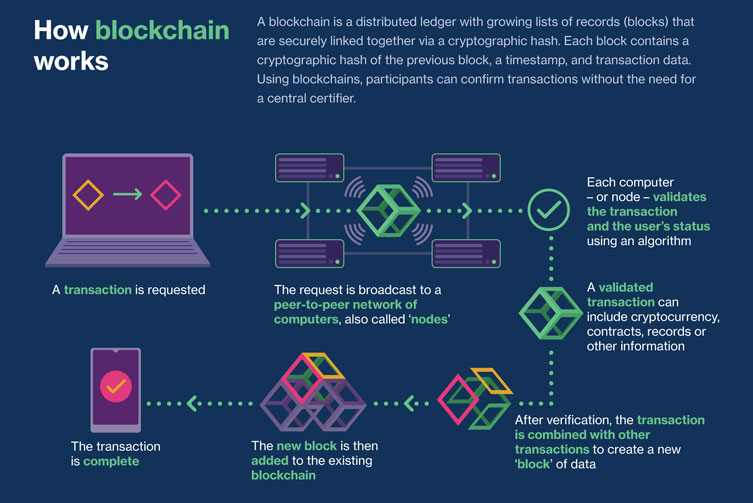
Blockchain applications differ a bit from DLT applications. For valid transaction requests executed, data is stored in a chain of blocks of transaction starting with a special block called the genesis block, such that the latest block cannot be deleted – unless there is consensus of the majority and the block before it is deleted and so on. This makes saved data relatively tamper-proof. Further differences include restrictions in DLT compared to Blockchain on who can submit requests and who can participate in the consensus processes.
Implementations
Many successful B2B applications in regulated industries use DLT which enables better privacy, compared to Blockchains where governance is less defined due to the lack of a central party. When there is one central party among the multiple parties, it is easy for such a central party to drive the collaboration among other parties and actualise the potential value of the technology. JP Morgan’s JPM-Coin is an inter-enterprise example while the Central Bank Digital Currency (CBDC) deployments, such as the one being piloted by the Reserve Bank of India, are also DLT-based.
When there is no central party among the multiple parties, it is difficult for the parties to collaborate to actualise the potential value of the technology. Success has typically come when industry associations and similar bodies form consortiums and drive collaboration. But independent of any technology, collaboration between competitors is always difficult. However, once the skills of creating and managing consortiums are developed by potential ecosystem anchors, the number of successful implementations will increase. One of the successful implementations of this kind is SPUNTA inter-bank reconciliation system in Italy which has over 90% of the country’s banks as participants.
Challenges and Opportunities
There have been several failures of DLT based B2B implementations in the recent past. Some of these have been unrelated to technology, like the lack of collaboration among competitors, but another reason seems to be that B2B businesses see the storing and routing of data (even if it is encrypted) by a DLT network and application provider as a business risk. There is the fear that a provider might change the balance of power and become a new power centre in the industry.
In the TCS view, providers should provide shared infrastructure and services to enable groups of B2B parties to create and own applications to automate multi-party processes, while storing and exchanging the data outside their shared infrastructure and enabling such applications to be migratable out of one shared infrastructure into to other similar shared infrastructure, if needed.
TCS has been working in this technology across multiple industries, using multiple DLT and Blockchain technology platforms including its own Quartz technology platform. In the insurance sector, TCS is working with multiple partners to consider options to create shared DLT/Blockchain infrastructure and provide services to enable the potential of this technology. We believe that this is one way to accelerate the adoption and value realisation of DLT/Blockchain technology.
Pratap Tambe is Engagement Director, Consulting and Service Integration, Tata Consultancy Services